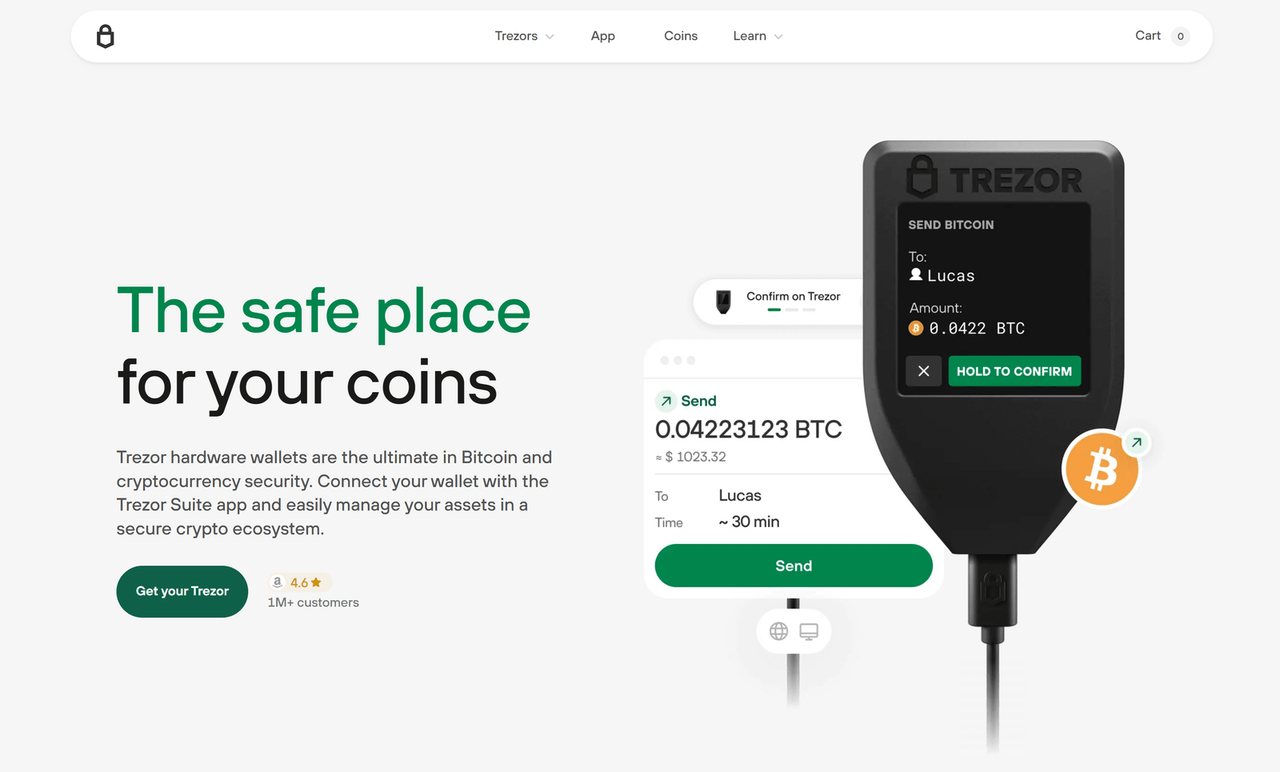
Securing Your Exchange Access via Trezor Login: The Ultimate Crypto Safety Move
In a world where cyber threats are constantly evolving, Securing Your Exchange Access via Trezor Login has become one of the most effective ways to protect your digital assets. Whether you’re trading daily or simply holding long-term investments, using a hardware wallet to log in adds a critical security layer that software solutions can’t match.
Why Securing Your Exchange Access via Trezor Login Matters More Than Ever
With phishing attacks, data breaches, and password leaks becoming commonplace, Securing Your Exchange Access via Trezor Login is no longer optional — it's essential. Exchanges like Binance, Kraken, and Bitstamp support external wallet-based login methods to prevent unauthorized access even if your account credentials are compromised.
How Securing Your Exchange Access via Trezor Login Works
Securing Your Exchange Access via Trezor Login involves connecting your Trezor hardware wallet to a supported platform, allowing you to verify login requests through the physical device. This ensures only someone with the actual Trezor in hand — and its PIN — can gain access.
Here's a high-level overview of how Securing Your Exchange Access via Trezor Login functions:
- You initiate login on a supported exchange platform.
- The exchange redirects you to a login request on Trezor.
- You confirm the action by physically pressing a button or verifying on the touchscreen (Model T).
- Access is granted — no password needed, and phishing links are rendered useless.
Compatible Platforms for Securing Your Exchange Access via Trezor Login
Not every exchange allows it yet, but support for Securing Your Exchange Access via Trezor Login is growing. Some of the most notable platforms include:
- Kraken (via FIDO2 or U2F integration)
- Binance (via WebAuthn or third-party integration)
- Bitstamp
- MyEtherWallet (MEW)
- MetaMask + Connected DApps
Using any of these services, Securing Your Exchange Access via Trezor Login boosts your protection against SIM-swapping, credential stuffing, and fake login portals.
Setting Up: A Quick Guide to Securing Your Exchange Access via Trezor Login
If you’re ready to take action, follow these basic steps to start Securing Your Exchange Access via Trezor Login today:
Step 1: Update Your Firmware and Trezor Suite
Before you begin Securing Your Exchange Access via Trezor Login, ensure your Trezor device is updated to the latest firmware. Open Trezor Suite and check for updates.
Step 2: Enable FIDO2/WebAuthn (if applicable)
Many platforms that support Securing Your Exchange Access via Trezor Login use the WebAuthn or FIDO2 protocols. Enable these in your exchange’s security settings.
Step 3: Register Your Trezor as a Security Key
Connect your Trezor, log in to your exchange’s security center, and register it as a 2FA device or WebAuthn login method. Now, Securing Your Exchange Access via Trezor Login is tied directly to your hardware wallet.
Key Advantages of Securing Your Exchange Access via Trezor Login
There are several significant benefits that come with Securing Your Exchange Access via Trezor Login, especially when compared to traditional 2FA tools like SMS or authenticator apps.
- Physical Security: Unlike mobile-based apps, Securing Your Exchange Access via Trezor Login requires physical possession of the hardware wallet.
- Phishing Protection: You can't approve a fake login if it doesn't come from the correct domain, making Securing Your Exchange Access via Trezor Login highly resistant to scams.
- No Password Reuse Risks: Since you don’t enter passwords, Securing Your Exchange Access via Trezor Login helps eliminate one of the biggest human-related vulnerabilities.
Limitations to Consider When Securing Your Exchange Access via Trezor Login
Despite its strengths, Securing Your Exchange Access via Trezor Login isn't without limitations:
- Platform Support: Not all crypto exchanges support this method yet.
- Initial Setup Complexity: For first-time users, Securing Your Exchange Access via Trezor Login can involve multiple setup steps that might feel overwhelming.
- Device Dependence: If you lose your Trezor or it’s damaged, recovering access could be time-consuming unless you’ve backed up your recovery seed securely.
Tips to Maximize Security While Securing Your Exchange Access via Trezor Login
Here are some best practices for making the most out of Securing Your Exchange Access via Trezor Login:
- Always verify domain names before connecting your device.
- Use Trezor with Trezor Suite and stick to official browser extensions only.
- Backup your seed phrase securely — Securing Your Exchange Access via Trezor Login won’t help if your recovery phrase is lost.
- Combine with other tools, like VPNs and IP whitelists, for layered protection.
Future of Crypto Security: Securing Your Exchange Access via Trezor Login Is Just the Start
The rise in hardware wallet adoption shows that Securing Your Exchange Access via Trezor Login is a part of a broader movement toward decentralized and hardware-based security. As Web3 platforms grow, expect more dApps, DeFi tools, and exchanges to support this method of access.
In the future, Securing Your Exchange Access via Trezor Login might expand into full-fledged identity authentication systems, helping users manage everything from financial accounts to decentralized profiles.
Final Thoughts: Why Securing Your Exchange Access via Trezor Login Is Worth It
When it comes to protecting your crypto holdings, Securing Your Exchange Access via Trezor Login is one of the smartest and most effective strategies you can implement today. It not only safeguards your exchange accounts but also gives you peace of mind that your assets are protected by hardware-level encryption and real-world authentication methods.
Whether you're a beginner or a veteran trader, Securing Your Exchange Access via Trezor Login offers a secure, modern, and phishing-resistant way to manage your accounts in a volatile digital landscape.